 | ||||






 | ||||
|
WELCOME TO THE ESSAY ARCHIVES!
<< June
<< Part I
(June/July)
<< June
<< June
<< June
<< Part I
(June/July)
* * *
|
2006 Essays - September
"Soon we could have Big Brother and Big Business tuning to the same frequency for not only will they know where you are, but they'll know what you're wearing." (n2) **Over the last three years, many of the site's articles have been "interactive" in the sense that the reader can go back and forth between the essay text and various information-related links embedded with it. By clicking a link the reader can learn more about a particular subject being discussed, then return to the essay by clicking the browser's "back" arrow. (The links are included for information purposes only. No guarantees are made as to the accuracy of the materials presented on the sites, although every effort has been made to search out reliable and respected sources of information. Also, certain product names are listed for illustrative purposes only. They do not constitute an endorsement of the product or service offered by the company mentioned.) Footnotes, a list of links and a bibliography are also included at the end of the text for anyone wishing to learn more about the subject. The materials presented here are only a small fraction of what is available on the topic of RFID technology. A glossary link has been provided as a reference for use as needed. Click here to reach the glossary.** Picture the following possible day: You walk out of the house one morning and step into your new Ford car. You stick the key in the ignition and start the car, knowing that the security system will be disabled as soon as the key is in place. On the way to work, you stop at a Mobil station. You wave your SpeedPass at the pump to activate it, fill up the tank and head to the freeway. Traffic is at a standstill, and you slowly maneuver your way to the less-crowded toll lanes. The morning's toll is automatically deducted from your account via the transponder you have attached to the top of your dashboard. After you use your personal security card to gain access to your office building and grab a cup of coffee, you head to your office. On your desk is your new passport, just issued by the State Department, so you can attend the company-wide meeting in Japan next month. After a long day's work, you stop at Wal-Mart to pick up a few items which have just been unloaded from their pallets and placed on the shelf. You drive home, stopping only briefly at the mailbox to pick up the day's mail, in which you find the envelope you've been waiting for. The envelope contains the chip you'll need to attach to your shoes when you run the local marathon the coming weekend. You're tired, and you fall asleep as soon as your head hits the pillow, not knowing that in that one day alone you've had as many as seven encounters with RFID technology. RFID, or Radio Frequency Identification, is not a new technology. "Radar was the technological precursor to RFID," (n3) and it "was first employed during WWII when it was used to help identify Allied planes from opposition aircraft." (n4) In its simplest sense, RFID "is a generic term for a set of technologies that use radio frequency (RF) to communicate data (a central component of which is an identity - specifically, a unique number)." (n5) Although its uses in the past may have been limited, advances in semiconductor technology (n6), coupled with powerful computing capabilities and the resources of the internet, have combined to expand the list of its potential uses. One of RFID's primary benefits is that it is a contactless technology - items containing RFID chips can be read from distances ranging from several inches to hundreds of feet away. Products do not need line-of-sight scanning, as a bar code need its laser reader. This contactless reading ability makes it adaptable to uses as diverse as automobile security systems, gas pump activation, toll collection, retail supply chain management and certain sporting activities, not to mention ID document monitoring (ie. passports, access cards, ID cards, etc.). The technology alternately has been hailed by its admirers as the "next big thing" in retailing and cursed by its critics as the coming of "Big Brother," and there are justifiable concerns about personal privacy when it comes to RFID use. This final essay of 2006 will look at some of the ABCs of RFID technology, a few of its current and potential uses, and issues of consumer and information privacy frequently cited in the context use of RFID technologies. (If you'd like to read a bit more about the history of RFID, click here.) COMPONENTS OF RFID SYSTEMS
Source: United States Government Accountability Office, Information Security: Key Considerations Related to Federal Implementation of Radio Frequency Identification Technology, GAO-05-849T, a report to the Subcommittee on Economic Security, Infrastructure, Protection and Cybersecurity, House Committee on Homeland Security, June 22, 2005, Highlights. The primary components of an RFID system are a tag (transponder), a reader (which uses radio frequency to communicate with the tag and converts the information to digital format), and the components (databases, etc.) necessary for managing the data collected and linking it to other pertinent information. (This is also referred to as the back-end portion of the system). Tags An RFID tag, also known as a transponder, consists of a chip and an antenna. The chip stores a unique serial number or other information based on its type of memory. The antenna, which is attached to the microchip, transmits information through the air to the reader in the form of radio waves. The tag can be either attached to or embedded in the object to be identified, whether an individual item of pallet of goods (readers can read multiple tags simultaneously). (n7) There are two primary types of RFID tags/transponders, passive and active. Although there are several subsets of both categories, only the broadest definitions of two types are included here. 1) Passive tags: "Passive tags/transponders have no energy source of their own, relying on energy given off by the reader for the power to respond." (n8) These tags generally cost less, operate at lower frequencies, and must be in relatively close proximity to the reader in order to be read. The simplest passive tags hold only a unique indentifier and no other . . . information. When a reader reads the tag's ID, it typically uses the ID to index a database that contains more expansive information about the object. For example, a tag on a package of pharmaceuticals may point to a database entry about the provenance of the drugs in the package, the distribution history of the package and its final destination." (n9) 2) Active tags: Active tags "contain a power source (battery) and a transmitter, in addition to the antenna and chip, and send a continuous signal. These tags typically have read/write capabilities - tag data can be rewritten or modified. Active tags can initiate communication and communicate over longer distances." (n10) Such tags generally are higher priced, operate at higher frequencies and may be read from distances which are hundreds of feet away (or more). Readers A reader is "a scanning device that is capable of reliably reading tags and communicating the results to a database. A reader uses its own antenna to communicate with the tag. When a reader broadcasts radio waves, all tags designated to respond to that frequency and within range will respond . . . Readers can process multiple items at once . .. [and] are differentiated by their storage capacity, processing capability and the frequencies they can read." (n11) Readers may be selected based on the particular application(s) for which they are to be used. "Low frequency RFID systems use less power and are better able to penetrate non-metallic substances . . . Higher frequencies typically use more power and are less likely to pass through materials." (n12) The readers can be either hand-held or stationary. Databases Although the database which ultimately contains information on a tag or range of RFID tags is generally referred to as the "back-end" portion of the system, it is the locus of the most significant information relating to the monitored items. This database "tracks and contains information about the tagged item . . . and can also be linked to other networks . . . which can connect the database to the Internet. This connectivity can allow for data sharing beyond the local database from which the information was originally collected." (n13) Click on the following links if you'd like to read more about "What is RFID?" or "RFID Basics" before continuing. The number of possible applications of RFID technology in business, consumer and government markets are seemingly endless and will be discussed in greater depth later in the essay. Two of the largest users of RFID systems at this time are Wal-Mart and the U.S. Government/Department of Defense. Both organizations have issued mandates forcing their major suppliers to include RFID tags on pallets of goods destined for their distribution and retail centers. This perhaps promted even more rapid use of the technology than what might otherwise have happened. However, aside from the the U.S. Government and Wal-Mart, businesses and other organizations in general had begun to express an interest in RFID in the late 1990s due perceived inadquacies in the existing bar code system.
Photograph "Perth, Australia" © 1985 Dorothy A. Birsic ELECTRONIC PRODUCT CODE (EPC) The barcode celebrated its 30th birthday in 2004. (n14) Although the bar code system "was the first successful model for mechanized inventory control," (n15) and is used worldwide, several disadvantages inherent in the barcode system began to emerge in the 1990s. "First, they (barcodes) are limited in terms of the amount of information they can carry. Second, they are far too easily smudged, damaged, or lost. Third, and perhaps most important, they require physical scanning and must therefore be visible and accessible to the scanning device, which implies that the package[s] on which they are printed must be oriented in a particular way as [they] pass through the scanner, a process that often involves human intervention -- and therefore added cost." (n16) In 1999, a joint industry-academic consortium call the Auto-ID Center formed at MIT. The group began working on RFID standards which could be used globally (n17), as well as an Internet - based system to identify products anywhere in the world through the use of an electronic product code (EPC). In 2003, the Auto-ID center became Auto-ID Labs (http://autoid.mit.edu/cs), and administrative functions were taken over by EPCglobal. (www.epcglobalinc.org) EPCglobal is "a non-profit, industry-based organization that operates with the stated goal of establishing and supporting the use of EPC technologies and networks as the global standard for immediate, automatic and accurate product identification." (n18) Some refer to the EPC as "the Internet of inventory, or an ambitious scheme to create a global, standardized [RFID] network for tracking everything that is shipped, stocked or sold." (n19) There is no chance that the established bar code system will disappear any time soon. However, there are aspects of the EPC system which make it more adaptable to global markets in an Internet age. A standard EPC code has a "header followed by three data fields . . . By encoding the data as a series of fields, a[n] [RFID] scanner can conduct customized search routines, such as by manufacturer or by type." (n20) Another advantage of the system is the level of ID detail able to be obtained via EPCs. For example, under the current barcode system, "all bags of Oreos have the same barcode. Electronic Product Codes have so many digits that each bag [of Oreos] could receive its own [EPC number], as could up to a billion billion other items." (n21) In addition, the design of EPCs "is based on the Domain Name Service (DNS) used in the Internet to locate an address," (n22) and the system can direct inquiries from computers to an IP address where information about a particular product [that was collected from a reader] is archived. The EPCglobal Inc. report "The EPC Global Architecture Framework" is available at www.epcglobalinc.org. It broadly defines the principles, standards and components necessary to successfully develop and implement the EPCglobal network. Anyone interested in learning more about how RFID and EPCs could apply to their business also may want to visit the EPCglobal U.S. website, www.epcglobalus.org. The organization's annual conference will be held in Los Angeles next month (Oct. 17 - 19) at the Los Angeles Convention Center. What might all this lead to? The "holy grail" (n23) of RFID retail applications is the checkout-less grocery store of the future. In such a store you'd shop the aisles much as you do now, placing groceries of all shapes and sizes in the cart in front of you. When you're finished, you would walk down a corridor (or some type of area) equipped with RFID readers, which would read all the tags on items in your cart as you walked by. You would either pay at the exit, or you'd walk directly to your car after an RFID reader scanned your payment card and automatically deducted the amount due from your account. This application, if it ever materializes, is still a long-term goal. Most RFID tagging in retail is still at a pallet- or case-level and not at an individual item level. At a "current price of about 20 - 30 cents per tag for [passive] item-level tags," (n24) the cost is still too high for many companies to justify the expense. By some estimates the price of tags would have to drop to about five cents before they would become feasible for use at an item level. (n25) Even at that, retail industry trade representatives have testified that "widespread item-level RFID tagging is a decade or more in the future. In fact, the proposition is so costly that a leading technology firm does not see widespread tagging of items costing less than ten dollars until 2017 at the earliest." (n26) But what about now, you might ask? Are there any current uses of RFID beyond the tagging of pallets of goods being shipped across the nation or globally? CURRENT APPLICATIONS OF RFID TECHNOLOGY
Photograph © 2009 Dorothy A. Birsic
For those of you who read last month's VOIP essay, here's also one last application tying that technology in with RFID. "Mitsukoshi, one of Japan's leading luxury department stores, spent the better part of 2005 piloting the use of RFID tags in the ladies' shoe department. . . On January 31 of this year, the retailer and Fujitsu Limited launched a new RFID pilot called 'Department Store of the Future' on the second floor of their Ginza store. In their New York Runway shop, RFID tags are attached to approximately 5000 pairs of better jeans. . . In addition to two other uses of the tags, six 'intelligent fitting rooms' are equipped with LCD panels that have built-in IP telephones and RFID tag - reader functionality. These 'intelligent rooms' provide the chance for customers to check size and color availability. The system also allows the customer to telephone an associate and intiate a request for the associate to retrieve alternate sizes and styles." (n31) The lists are seemingly endless, from "smart shelves" that can "read" product availability and handle inventory control, to bracelets for the monitoring of patients and patient medication in hospitals. Click on the following links to read two other brief articles on Consumer Applications and Benefits and RFID Business Applications. As was alluded to earlier, the potential uses for RFID chips extend beyond business and consumer applications. With the exception, perhaps, of implanting RFID chips in humans, few applications raise as much concern about the arrival of "Big Brother" as the inclusion of RFID chips in official identification documents such as drivers licenses or passports. THE NEW U.S. ePASSPORT In February of 2005 the Department of State published proposed rules in the Federal Register to amend passport regulations to include provisions for introducing "electronic passports." (n32) These electronic passports, usually referred to as ePassports, are enhanced versions of a traditional passport which use an embedded electronic chip to digitally carry the same information included on the data page, a (digital) biometric version of the bearer's photo, and coding to prevent any digital data from being altered or removed. Those ePassports have begun being issued as of earlier this month. Current passports will be valid until their expiration date, at which point they will be replaced by an ePassport when renewed. Although widely reported as containing RFID tags, the passports incorporate a similar, though slightly different, technology. "The technology selected for the electronic passport is the 64 kilobyte contactless integrated circuit chip (ICC) with an antenna. The electronic chip itself has a short read distance, approximately four inches." (n33) The difference between the ICC and RFID is that the chips are based on an international standard (ISO/IEC 14443) for contactless chips and cards that can be read at a distance of less than 10 centimeters (4 inches) and operate at 13.56KHz. (n34) In addition, the ICC technology "not only supports security features that ensure the integrity, confidentiality and privacy of information stored on or transmitted by the card, but also provides features that can verify the authenticity of the card and its contents, preventing tampering and forgeries." (35) Some of these capabilities are not supported on regular RFID chips. Changes being made to the U.S. passports are in line with international requirements and standards as set forth by the U.N.-affiliated International Civil Aviation Organization (ICAO, www.icao.int). The ICAO has also introduced a new international symbol which will make it easier to automatically identify ePassports throughout the world. The symbol "consists of a small circle enclosed by two horizontal rectangles, representing the chip sandwiched between two layers of material . . . On seeing the symbol, an inspector [will] know that the document contains a chip, that it should be inspected using electronic equipment, and that it should be treated with care." (n36) A diagram of that symbol is included below, along with an indication of its placement on the cover of a typical U.S. tourist passport.
Source: United States Department of State and the International Civil Aviation Organization (ICAO) The State Department has established a section of their website giving information on the new passports, as well as a full animated view of the inner pages of the document. Click on the either of the following links to reach the pages: State Departement ePassport website page and State Department ePassport animation. Of the ICAO's 188 contracting states, 41 so far have publicly indicated their intention to upgrade to ePassports in the next two years. (n37) At the time of the initial State Department notice of the proposed rule change for the electronic passport, comments from the public were accepted for 45 days. All of the comments received, both by regular mail and by e-mail, are available on the State Department ePassport website. Among the groups objecting to the new documents were the American Civil Liberties Union (ACLU) and the Electronic Frontier Foundation (EFF). The ACLU's statement to the State Department can be found on the ACLU website. Many comments focused on perceived violations of individual privacy due to the new documents, and some questioned whether or not the ePassports would provide any greater security than those already in existence. In an interview which appeared the same day as the date of the ACLU's comments to the State Department, Barry Steinhardt, the Director of ACLU's Program on Technology and Liberty, explained a bit more about his organization's position on RF technologies. He also gave the following warning: "There are huge volumes of data eventually being collected, both because of data stored with the [identity] card itself and because of the database that the [identity] card will be linked to. It will enable essentially universal monitoring and tracking. It hurtles us down the path toward the surveillance society, where you will not be able to engage in any transaction without having your actions recorded, your background checked, [your privacy] violated." (n38) RFID AND PRIVACY The potential benefits from use of RFID technologies are great, but the potential for abuse of RFID systems is also quite real. At this stage of RFID deployment, when the majority of applications still are within product supply chains, and the main uses are for tracking products from manufacturer to the market, there are "limited implications with respect to cultural and social values. [However], once tags are embedded in individual products, privacy and trust concerns become more salient . . . When thinking through those issues, it is crucial to understand when individual identity becomes associated with a tag (or data within the system), whether that needs to happen, and what the implications are." (n39). Different organizations approach the issues from a variety of perspectives. The obvious proponent of the EPC system, EPCglobal, posts its consumer policies for RFID technology to its website (www.epcglobalinc.org). The Electronic Frontier Foundation (EFF), often an opponent of RFID use, has a section of the EFF website specifically for RFID issues. That section can be found at www.eff.org/Privacy/Surveillance/RFID. The organization also has published a position paper on the use of RFID in consumer products. To read that position paper, click here, or go directly to the EFF website. Another group, the Privacy Rights Clearinghouse, delineates five specific potential threats to privacy and civil liberties from the use of RFID. These include "the hidden placement of tags, unique identifiers for all objects worldwide (via EPCs) which would enable every object on earth to have its own ID, massive data aggregation, hidden readers (making it virtually impossible for a consumer to know when or if he or she was being "scanned"), and individual tracking and profiling." (n40). The organization's full RFID position statement and framework for RFID rights and responsibilities can be found at www.privacyrights.org/ar/RFIDposition.htm. One of the first state bills to be passed dealing specifically with RFID matters was just approved by the California State Senate on August 31, 2006. Senate Bill (SB) 768, the Identity Information Protection Act of 2006, will require privacy and security measures for RFID tags in state ID cards. The bill was passed by the Assembly earlier in the year, and Governor Schwarzenegger has until September 30 to sign it. (n41). Further information on the bill can be found at the EFF website or by clicking "Legislation" at www.senate.ca.gov and searching under SB 768. In the rapidly changing digital world, "ethical, legal and social issues related to RFID technologies reflect some of the same concerns raised about other emerging, wireless and embedded technologies" (n42) on the horizon. Developing the ability to address the concerns "will be an important strategy for all stakeholders as the technology moves forward." (n43). Opportunities to learn more about RFID abound. In the local UC system, both UCI and UCLA offer RFID-related seminars and courses. UCI has established a series of RFID courses in its Extension program, and UCLA's Wireless Internet for the Mobile Enterprise Consortium, or WINMEC (www.winmec.ucla.edu), offers a series of regular seminars on the subject. Details on their October program can be found at www.winmec.ucla.edu/rfid/experience/Oct2006.
n1 - Want, Roy, "RFID: A Key to Automating Everything," Scientific American, Vol. 290, No. 1, January 2004, p. 58 (*) n2 - Schakowsky, Janice D., opening remarks in "RFID Technology: What the Future Holds for Commerce, Security and the Consumer," hearing before the Subcommittee on Commerce, Trade and Consumer Protection, Committee on Energy and Commerce, U.S. House of Representatives, 108th Congress, Second Session, July 14, 2004, Serial Number 108-108, Washington, D.C.: U.S. Government Printing Office (GPO), 2004, p. 3 (*) n3 - Shepard, Steven. RFID: Radio Frequency Identification. New York: McGraw-Hill, 2005, p. 42 (*) n4 - Dillman, Linda, statement in "RFID Technology: What the Future Holds for Commerce, Security and the Consumer," hearing before the Subcommittee on Commerce, Trade and Consumer Protection, Committee on Energy and Commerce, U.S. House of Representatives, 108th Congress, Second Session, July 14, 2004, Serial Number 108-108, Washington, D.C.: U.S. Government Printing Office (GPO), 2004, p. 15 (*) n5 - Committee on Radio Frequency Identification (RFID), Computer Science and Telecommunications Board (CSTB), Division of Engineering and Physical Sciences, National Research Council (NRC) of the National Academies, Radio Frequency Identification Technologies: A Workshop Summary, Washington D.C.: National Academies Press, 2004, p. 1. Also available online at: http://www.nap.edu/catalog/11189.html. (*) n7 - U.S. Government Accountability Office, Information Security: Key Considerations Related to Federal Implementation of Radio Frequency Identification Technology, GAO-05-849T, a report to the Subcommittee on Economic Security, Infrastructure, Protection and Cybersecurity, House Committee on Homeland Security, June 22, 2005, Washington D.C.: U.S. GAO, 2005, p. 4 (*) n8 - Harper, Jim, "RFID Tags and Privacy: How Bar-Codes-On-Steroids are Really a 98-lb. Weakling," CEI-N Point, Vol. 89, June 21, 2004, Washington D.C: Competitive Enterprise Institute, 2004, p. 2 (*) n9 - Committee on RFID, CSTB, Division of Engineering and Physical Sciences, NRC of the National Academies, p. 4 (*) n10 - U.S. Government Accountability Office, GAO-05-849T, p. 5 (*) n13 - U.S Government Accountability Office, GAO-05-849T, p. 6 (*) n14 - Roush, Wade, "Beyond the Barcode," Technology Review, Vol. 107, No. 10, December 2004, p. 20 (*) n15 - Shepard, Steven, p. 39 (*) n17 - Committee on RFID, CSTB, Division of Engineering and Physical Sciences, NRC of the National Academies, p. 12 (*) n24 - McKinley, Ed, "To the Shelves - and Beyond," Stores, Vol. 87, No. 9, September 2005, p. 34 (*) n26 - Retail Industry Leaders Association, prepared statement, in "RFID Technology: What the Future Holds for Commerce, Security and the Consumer," hearing before the Subcommittee on Commerce, Trade and Consumer Protection, Committee on Energy and Commerce, U.S. House of Representatives, 108th Congress, Second Session, July 14, 2004, Serial Number 108-108, Washington, D.C.: U.S. Government Printing Office (GPO), 2004, p. 69 (*) n27 - Committee on RFID, CSTB, Division of Engineering and Physical Sciences, NRC of the National Academies, p. 15 (Items #1-5a) (*) n28 - Murray, Charles, "Implanted RFID Chips Get FDA Approval," EE (Electronic Engineering) Times, Issue 1343, October 18, 2004, p. 8 (*) n29 - "Radiofrequency Identification: Protecting the Drug Supply," FDA Consumer, Vol. 39. No. 2, March-April 2005, p. 37 (*) n30 - Reda, Susan, "What You Don't Know About RFID," Stores, Vol. 87, No. 9, September 2005, p. 27 (Items #6 - 10) (*) n31 - Reda, Susan, "Stepping Up the RFID Effort," Stores, Vol. 88, No. 3, March 2006, pp. 26 - 27 (*) n32 - U.S. Department of State, Public Notice 4993, RIN 1400-AB93, Federal Register, Vol. 70, No. 33, February 18, 2005, pp. 8305 - 8309 (*) n34 - Smart Card Alliance Identity Council, "Western Hemisphere Travel Initiative PASS Card: Recommendations for Using Secure Contactless Technology vs. RFID," Smart Card Alliance, 2006, p. 6. Document available/viewed 8/2006 at www.ti.com/rfid/docs/manuals/whtpapers/wp-recommendations_for_using_contactless.pdf (*) n36 - Broekhaar, Sjef, "New Symbol Allows ePassport to be Recognized Instantly," International Civil Aviation Organization (ICAO) MRTD Report, Vol. 1, No. 1, 2006, pp. 29 - 30. Available/viewed online 8/2006 at ww.icao.int/cgi/goto_m_atb.pl?icao/en/atb/fa./mrtd/MRTD_Rpt_v1n1_2006.pdf (*) n37 - ICAO, ICAO MRTD Report, Vol. 1, No. 1, 2006, pp. 32 & 34 (*) n38 - Yoshida, Junko, "Sending the Alarm as Big Brother Goes Digital," EE (Electronic Engineering) Times, Issue #1365, April 4, 2005, p. 14 (*) n39 - Committee on RFID, CSTB, Division of Engineering and Physical Sciences, NRC of the National Academies, p. 24 (*) n40 - Privacy Rights Clearinghouse, RFID Position Statement of Consumer Privacy and Civil Liberties Organizations, viewed online August 2006 at www.privacyrights.org/ar/RFIDposition.htm (*) n41 - Viewed online at www.eff.org September 1, 2006 (*) n42 - Committee on RFID, CSTB, Division of Engineering and Physical Sciences, NRC of the National Academies, p. 27(*) LINKS INCLUDED IN ESSAY
BIBLIOGRAPHY - The following is the bibliography for the September 2006 essay on RFID. Broekhaar, Sjef. "New Symbol Allows ePassport to be Recognized Instantly," International Civil Aviation Organization (ICAO) MRTD Report, Vol. 1, No. 1, 2006, pp. 29 - 31. Available/viewed online 8/2006 at ww.icao.int/cgi/goto_m_atb.pl?icao/en/atb/fa./mrtd/MRTD_Rpt_v1n1_2006.pdf Committee on Radio Frequency Identification (RFID), Computer Science and Telecommunications Board (CSTB), Division of Engineering and Physical Sciences, National Research Council (NRC) of the National Academies. Radio Frequency Identification Technologies: A Workshop Summary, Washington D.C.: National Academies Press, 2004. Also available online at: http://www.nap.edu/catalog/11189.html. Dillman, Linda, statement in "RFID Technology: What the Future Holds for Commerce, Security and the Consumer," hearing before the Subcommittee on Commerce, Trade and Consumer Protection, Committee on Energy and Commerce, U.S. House of Representatives, 108th Congress, Second Session, July 14, 2004, Serial Number 108-108, Washington, D.C.: U.S. Government Printing Office (GPO), 2004 Harper, Jim. "RFID Tags and Privacy: How Bar-Codes-On-Steroids are Really a 98-lb. Weakling," CEI-N Point, Vol. 89, June 21, 2004, Washington D.C: Competitive Enterprise Institute, 2004 ICAO, ICAO MRTD Report, Vol. 1, No. 1, 2006, pp. 32 & 34 McKinley, Ed, "To the Shelves - and Beyond," Stores, Vol. 87, No. 9, September 2005, pp. 32 - 34 Murray, Charles, "Implanted RFID Chips Get FDA Approval," EE (Electronic Engineering) Times, Issue 1343, October 18, 2004, p. 8 Privacy Rights Clearinghouse. RFID Position Statement of Consumer Privacy and Civil Liberties Organizations, viewed online August 2006 at www.privacyrights.org/ar/RFIDposition.htm Reda, Susan, "Stepping Up the RFID Effort," Stores, Vol. 88, No. 3, March 2006, pp. 26 - 30 Reda, Susan, "What You Don't Know About RFID," Stores, Vol. 87, No. 9, September 2005, pp. 26 - 27 Retail Industry Leaders Association, prepared statement, in "RFID Technology: What the Future Holds for Commerce, Security and the Consumer," hearing before the Subcommittee on Commerce, Trade and Consumer Protection, Committee on Energy and Commerce, U.S. House of Representatives, 108th Congress, Second Session, July 14, 2004, Serial Number 108-108, Washington, D.C.: U.S. Government Printing Office (GPO), 2004 Roush, Wade, "Beyond the Barcode," Technology Review, Vol. 107, No. 10, December 2004, pp. 20 - 21 Schakowsky, Janice D., opening remarks in "RFID Technology: What the Future Holds for Commerce, Security and the Consumer," hearing before the Subcommittee on Commerce, Trade and Consumer Protection, Committee on Energy and Commerce, U.S. House of Representatives, 108th Congress, Second Session, July 14, 2004, Serial Number 108-108, Washington, D.C.: U.S. Government Printing Office (GPO), 2004 Shepard, Steven. RFID: Radio Frequency Identification. New York: McGraw-Hill, 2005 Smart Card Alliance Identity Council, "Western Hemisphere Travel Initiative PASS Card: Recommendations for Using Secure Contactless Technology vs. RFID," Smart Card Alliance, 2006. Document available/viewed 8/2006 at www.ti.com/rfid/docs/manuals/whtpapers/wp-recommendations_for_using_contactless.pdf U.S. Department of State, Public Notice 4993, RIN 1400-AB93, Federal Register, Vol. 70, No. 33, February 18, 2005, pp. 8305 - 8309 U.S. Government Accountability Office, Information Security: Key Considerations Related to Federal Implementation of Radio Frequency Identification Technology, GAO-05-849T, a report to the Subcommittee on Economic Security, Infrastructure, Protection and Cybersecurity, House Committee on Homeland Security, June 22, 2005, Washington D.C.: U.S. GAO, 2005 U.S. Government Accountability Office, Information Security: Radio Frequency Identification Technology in the Federal Government, GAO-05-551, a report to the Congressional Requesters, May 2005, Washington D.C.: U.S. GAO, 2005 U.S. Government Accountability Office, Privacy: Key Challenges Facing Federal Agencies, GAO-06-777T, statement of Linda D. Koontz before the Subcommittee on Commercial and Administrative Law, Committee on the Judiciary, House of Representatives, May 17, 2006. Washington D.C.: U.S. GAO, 2006 Want, Roy, "RFID: A Key to Automating Everything," Scientific American, Vol. 290, No. 1, January 2004, pp. 56 - 65 Yoshida, Junko, "Sending the Alarm as Big Brother Goes Digital," EE (Electronic Engineering) Times, Issue #1365, April 4, 2005, pp. 1 & 14
To return to the top of the page, click here. To return to the essay archives, click here. Follow www.dorothyswebsite.org on TWITTER! Home | Poetry | Essays |
Free Concerts | Links | 2012 Extras |
About the Site |
|||
 | ||||
|
www.dorothyswebsite.org © 2003 - 2012 Dorothy A. Birsic. All rights reserved. Comments? Questions? Send an e-mail to: information@dorothyswebsite.org | ||||




 "The most profound technologies are those that disappear. They weave themselves into the fabric of everyday life until they are
indistinguishable from it."
"The most profound technologies are those that disappear. They weave themselves into the fabric of everyday life until they are
indistinguishable from it." 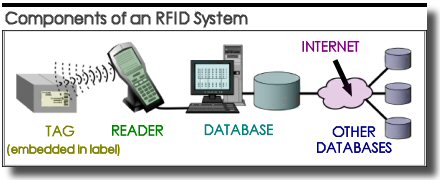

 Though widespread item-level tagging may be more than a decade away,
the number and variety of uses for RFID technology appear to be expanding rapidly. The following is a sampling of current uses and pilot tests which have been reported in the press over the last two years.
Though widespread item-level tagging may be more than a decade away,
the number and variety of uses for RFID technology appear to be expanding rapidly. The following is a sampling of current uses and pilot tests which have been reported in the press over the last two years.
 FOOTNOTES - The following are the footnotes
indicated in the text in parentheses with the letter "n" and a number. If
you click the asterisk at the end of the footnote, it will take you back
to the paragraph where you left off.
FOOTNOTES - The following are the footnotes
indicated in the text in parentheses with the letter "n" and a number. If
you click the asterisk at the end of the footnote, it will take you back
to the paragraph where you left off.
